Cloud Security
Unpacking my ‘go-to’ architecture for securing large scale highly connected digital assets.
This architecture reflects my current technical acumen and business philosophies:
- Customer is most important person in the room
- Do more with less
- Secure by design
- Learn & apply
- Follow the data
- Simplicity accelerates
I use it within my own projects — and as a baseline for related consulting work.
It’s an ideal — secure, performant and modular — platform for delivering:
- Compliance monitoring
- Automated threat identification
- Event-driven response
Inspired — and perpetually evolving — from AWS reference architectures and security best-practices:
- Principle of Least Privilege (PoLP)
- Ubiquitous encryption
- Automatic remediation
And continuously validated against the AWS Well-Architected and NIST Cybersecurity frameworks.
Push-Button Deployment
Maintained in a library of CloudFormation templates and deployable on-demand — as individual modules or end-to-end.
Design Considerations
- Why not TerraForm? CloudFormation covers everything required in a universal format (
YAML/JSON), so there is no compelling reason to take on the added costs and complexity of a 3rd-party tool - Why AWS? In a word…ecosystem. The breadth and quality of services, coupled with their integration, provide the most compelling business case. And after working with nearly all of AWS’s services over the past 10+ years — and applying their published best practices and reference architectures — AWS has earned my trust…and my business. I’ve also used GCP and Azure quite a bit, but have always ended up back on AWS due to performance or architectural reasons.
The Bigger Picture
This architecture also fills a key role in a more comprehensive cloud strategy:
So let’s dive in…
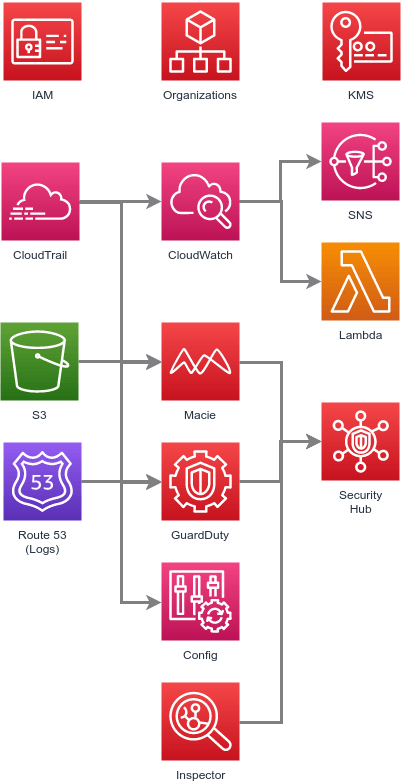
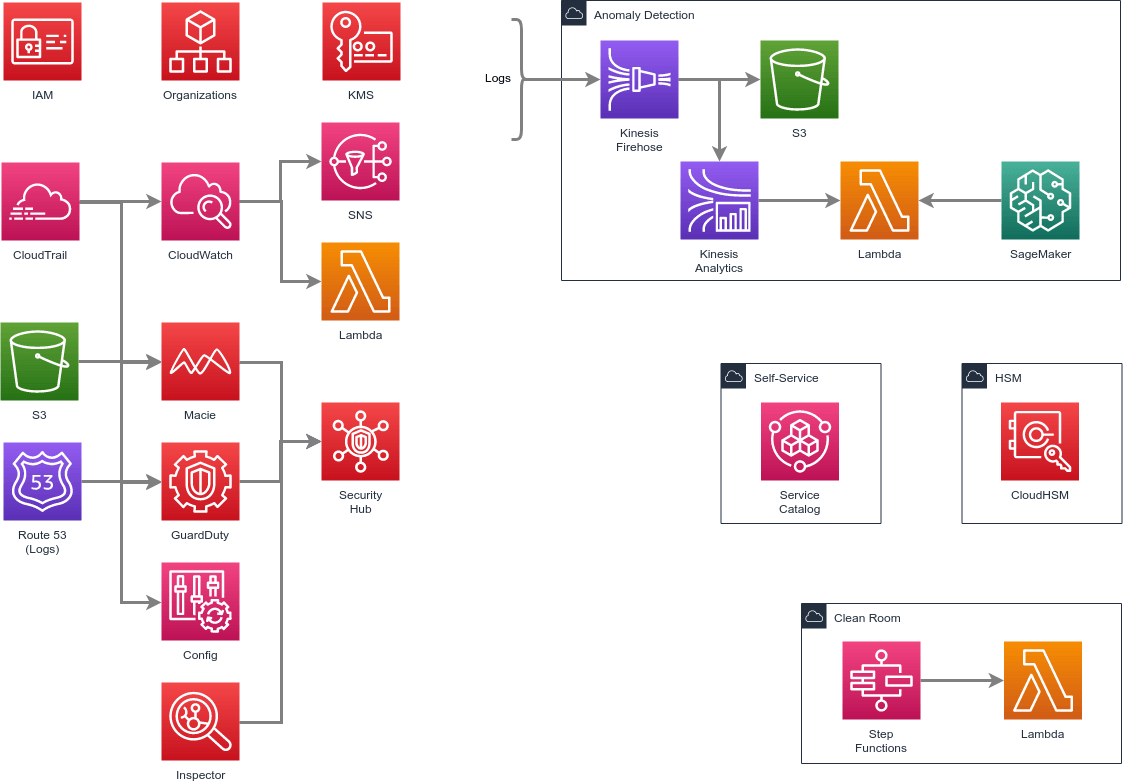
Core Components
Laying the groundwork for identity and access management, logging, monitoring — while optimizing for a multi-account environment.
- Organizations — Apply Service Control Policies (SCP) to manage individual accounts
- Identity & Access Management (IAM) — User and permissions
- CloudTrail — Log API calls
- Config — Monitor service configuration
- Security Hub — Aggregate security-related logs and notifications
- GuardDuty — Identify threat patterns
- Inspector — Identify vulnerabilities in EC2 instances
- Macie — Identify unsecured Personally Identifiable Information (PII)
- Key Management Service (KMS) — Encryption key management
- Simple Notification Service (SNS) — Fan out messages
- Lambda — Execute remediation tasks
- Simple Storage Service (S3) — Primary data storage
- Virtual Private Cloud (VPC) — Network-level isolation of resources and traffic (including Security Groups, NACLs, NAT, Route Tables, etc.)
- CloudWatch — Collect and store logs from Lambda
Automating best practices — least privilege, cross-account roles, etc.
Expansion Modules
With this solid foundation in place, we can easily enhance functionality using a number of different add-on modules:
- Anomaly Detection
- Self-Service
- Hardware Security Module (HSM)
Let’s dive a little deeper into those modules…
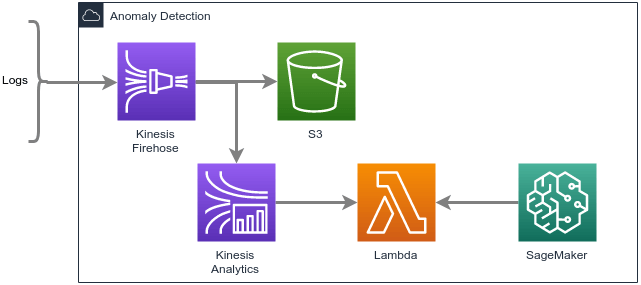
Anomaly Detection Service
Add-on microservice for ingesting and analyzing large volumes of logs (EC2 logs, VPC Flow Logs, etc.) in real time.
- Kinesis Data Firehose — Ingestion
- Kinesis Data Analytics — Anomaly detection
- Lambda — Respond to positive predictions
- Simple Storage Service (S3) — Storage of raw log files
- SageMaker — (optional) Decision automation
- CloudWatch — Collect and store logs from Lambda
Analyze streaming data and respond to anomalies in real time.

Self-Service Module
This add-on module provides a delegation framework and automation for quickly deploying approved cloud services.
- Service Catalog — Centrally manage catalog of services
Achieve consistent governance and meet compliance requirements.

Hardware Security Module (HSM)
This add-on module enables an HSM for encryption key management.
- CloudHSM — Hardware security module deployed into multiple Availability Zones.
KMS is usually my first choice, but stricter project requirements (FIPS 140-2 Level 3, single tenancy, etc.) may require an HSM.
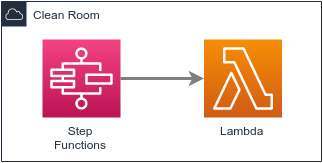
Clean Room
This add-on module enables a process for isolating a potentially compromised instance.
- Step Functions — Orchestrate actions
- Lambda — Execute actions
Automatically notify, isolate and run basic forensics on the instance.










